How To Find Ip Address Of Citrix Server
Duo integrates with your on-premises Citrix Gateway to add two-gene authentication to remote access logins. Duo Security supports inline self-service enrollment and Duo Prompt when logging on using a web browser. For Citrix Receiver or Workspace client connections, Duo Security supports passcodes, phone, and push hallmark.
If yous have Citrix Gateway build 12.1-51.16 or subsequently with an "Advanced" or "Premium" edition license, or Citrix Gateway build thirteen.0-67.ten or later with "Standard", "Avant-garde", or "Premium" edition license, attempt calculation Duo 2FA with nFactor.
If your users need the power to reset passwords from the Citrix Gateway and your Citrix edition license or Gateway build does not permit use of nFactor, meet the Citrix Gateway Bones Secondary Instructions.
Acquire more than about the differences between Duo's Citrix Gateway deployment configurations.
Overview
To add Duo two-gene hallmark to your Citrix Gateway you'll configure 2 RADIUS authentication policies — one that provides Duo's interactive enrollment and authentication prompts to browser-based Gateway logins, and a second one that responds to Receiver or Workspace client logins with an automated hallmark asking via push notification to a mobile device or a telephone call. In this configuration the Duo Hallmark Proxy handles both master and secondary authentication.
Citrix Gateway was formerly known as NetScaler Gateway. These instructions apply to both products.
Connectivity Requirements
This application communicates with Duo's service on TCP port 443. Firewall configurations that restrict outbound admission to Duo's service with rules using destination IP addresses or IP address ranges aren't recommended, since these may modify over time to maintain our service'due south high availability. If your organisation requires IP-based rules, please review this Duo KB article.
First Steps
Before moving on to the deployment steps, it's a proficient idea to familiarize yourself with Duo administration concepts and features similar options for applications, available methods for enrolling Duo users, and Duo policy settings and how to use them. See all Duo Administrator documentation.
Y'all should already have a working primary authentication configuration for your Citrix Gateway users before yous begin to deploy Duo.
To integrate Duo with your Citrix Gateway, y'all volition need to install a local Duo proxy service on a machine within your network. This Duo proxy server will receive incoming RADIUS requests from your Citrix Gateway, contact your existing local LDAP/Advertising or RADIUS server to perform chief hallmark, so contact Duo'southward deject service for secondary authentication.
Locate (or set) a arrangement on which y'all will install the Duo Authentication Proxy. The proxy supports these operating systems:
- Windows Server 2012 or later (Server 2016+ recommended)
- CentOS 7 or later (CentOS 8+ recommended)
- Red Hat Enterprise Linux vii or afterwards (RHEL eight+ recommended)
- Ubuntu sixteen.04 or afterward (Ubuntu eighteen.04+ recommended)
- Debian 7 or later (Debian 9+ recommended)
So you'll demand to:
- Sign up for a Duo business relationship.
- Log in to the Duo Admin Panel and navigate to Applications.
- Click Protect an Application and locate Citrix Gateway (NetScaler) in the applications list. Click Protect to get your integration key, secret fundamental, and API hostname. You'll need this data to complete your setup. See Protecting Applications for more data about protecting applications in Duo and additional application options.
Treat your underground key similar a password
The security of your Duo application is tied to the security of your cloak-and-dagger central (skey). Secure it as you would whatsoever sensitive credential. Don't share it with unauthorized individuals or email it to anyone under whatever circumstances!
Install the Duo Hallmark Proxy
The Duo Hallmark Proxy tin be installed on a physical or virtual host. We recommend a organisation with at to the lowest degree ane CPU, 200 MB disk infinite, and 4 GB RAM (although one GB RAM is unremarkably sufficient).
- Windows
- Linux
- Download the nearly recent Authentication Proxy for Windows from https://dl.duosecurity.com/duoauthproxy-latest.exe. Annotation that the actual filename will reverberate the version eastward.g. duoauthproxy-5.six.0.exe. View checksums for Duo downloads hither.
- Launch the Authentication Proxy installer on the target Windows server equally a user with administrator rights and follow the on-screen prompts.
When installing, yous can choose whether or not y'all desire to install the Proxy Manager. The Proxy Managing director is a Windows utility that helps you edit the Duo Authentication Proxy configuration, determine the proxy's status, and outset or stop the proxy service. Acquire more than about using the Proxy Manager. Installing the Proxy Director adds about 100 MB to the installed size.
If you do not want to install the Proxy Manager, you may deselect information technology on the "Choose Components" installer screen before clicking Install.
Silent Install
To perform a silent install on Windows, outcome the following from an elevated command prompt after downloading the installer (replacing version with the actual version you downloaded):
duoauthproxy-version.exe /South Append /exclude-auth-proxy-manager to install silently without the Proxy Manager:
duoauthproxy-version.exe /Due south /exclude-auth-proxy-manager -
Ensure that Perl and a compiler toolchain are installed. On most recent RPM-based distributions — similar Fedora, RedHat Enterprise, and CentOS — yous can install these by running (as root):
$ yum install gcc make libffi-devel perl zlib-devel diffutilsOn Debian-derived systems, install these dependencies past running (as root):
$ apt-get install build-essential libffi-dev perl zlib1g-devIf SELinux is nowadays on your system and y'all want the Authentication Proxy installer to build and install its SELinux module, include
selinux-policy-develin the dependencies:$ yum install gcc make libffi-devel perl zlib-devel diffutils selinux-policy-devel$ apt-become install build-essential libffi-dev perl zlib1g-dev selinux-policy-devel -
Download the near recent Authentication Proxy for Unix from https://dl.duosecurity.com/duoauthproxy-latest-src.tgz. From the command line y'all can use
scrollorwgetto download the file, like$ wget --content-disposition https://dl.duosecurity.com/duoauthproxy-latest-src.tgz. Depending on your download method, the bodily filename may reflect the version e.chiliad. duoauthproxy-5.6.0-src.tgz. View checksums for Duo downloads here. -
Extract the Authentication Proxy files and build it every bit follows:
$ tar xzf duoauthproxy-v.6.0-src.tgz $ cd duoauthproxy-version-src $ make -
Install the authentication proxy (as root):
$ cd duoauthproxy-build $ ./installFollow the prompts to complete the installation. The installer creates a user to run the proxy service and a grouping to own the log directory and files. You can take the default user and group names or enter your own.
If SELinux is present on the target server, the Duo installer will inquire you if you desire to install the Hallmark Proxy SELinux module. Your selection affects whether systemd tin first the Authentication Proxy after installation.
If you choose to install the Authentication Proxy SELinux module and the dependency
selinux-policy-develis non present then the installer fails to build the module.SELinux Way Default Response Result Enforcing Yes Choose 'yes' to install the Authentication Proxy's SELinux module. This permits start of the Authentication Proxy service past systemd. If y'all choose 'no' and then the SELinux module is non installed, and systemd cannot start the Authentication Proxy service. Permissive No Choose 'no' to decline install of the Authentication Proxy'due south SELinux module. The Authentication Proxy service can be started past systemd. All the same, if you modify SELinux from permissive to enforcing mode later on installing the Duo proxy, systemd can no longer get-go the Authentication Proxy service. If yous plan to enable SELinux enforcing mode later, you should choose 'aye' to install the Authentication Proxy SELinux module now.
Silent Install
To install the Duo proxy silently with the default options, use the post-obit command:
sudo ./duoauthproxy-build/install --install-dir /opt/duoauthproxy --service-user duo_authproxy_svc --log-grouping duo_authproxy_grp --create-init-script yes Append --enable-selinux=aye|no to the install command to choose whether to install the Authentication Proxy SELinux module.
Configure the Proxy
After the installation completes, you will need to configure the proxy.
The Duo Authentication Proxy configuration file is named authproxy.cfg, and is located in the conf subdirectory of the proxy installation. With default installation paths, the proxy configuration file will be located at:
| Operating System | Authentication Proxy Version | Path |
|---|---|---|
| Windows | v5.0.0 and afterward | C:\Program Files\Duo Security Authentication Proxy\conf\authproxy.cfg |
| Windows | v4.0.2 and before | C:\Programme Files (x86)\Duo Security Hallmark Proxy\conf\authproxy.cfg |
| Linux | All | /opt/duoauthproxy/conf/authproxy.cfg |
Notation that as of v4.0.0, the default file admission on Windows for the conf directory is restricted to the built-in Administrators group during installation.
The configuration file is formatted as a simple INI file. Section headings appear as:
[section] Individual properties beneath a section announced equally:
name=value The Authentication Proxy may include an existing authproxy.cfg with some instance content. For the purposes of these instructions, however, you should delete the existing content and showtime with a bare text file.
Duo Hallmark Proxy Managing director
The Duo Hallmark Proxy Manager is a Windows utility for managing the Authentication Proxy installation on the Windows server where y'all install the Authentication Proxy. The Proxy Manager comes with Duo Authentication Proxy for Windows version 5.6.0 and after.
The Proxy Manager cannot manage remote Duo Hallmark Proxy servers, nor can you lot install the Proxy Manager equally a stand-alone application. There is no Proxy Manager available for Linux. The Proxy Manager only functions as part of a local Duo Hallmark Proxy installation on Windows servers.
Acquire more about using the Proxy Manager in the Duo Authentication Proxy Reference before you continue.
To launch the Proxy Managing director utility:
- Open up the Start Carte and become to Duo Security.
- Click the Duo Authentication Proxy Manager icon to launch the application. Yous must have administrative privileges on the Windows server and accept the prompt for superlative.
- The Proxy Manager launches and automatically opens the
%ProgramFiles%\Duo Security Authentication Proxy\conf\authproxy.cfgfile for editing.
Use the Proxy Manager editor on the left to make the authproxy.cfg changes in these instructions. As you type into the editor, the Proxy Director will automatically suggest configuration options. Accepting these suggestions helps make certain you use the correct option syntax.
As you follow the instructions on this page to edit the Hallmark Proxy configuration, you can click Validate to verify your changes (output shown on the right).
When yous complete the Authentication Proxy configuration steps in this certificate, you tin utilise the Relieve button to write your updates to authproxy.cfg, and then use the authproxy.cfg push button to commencement the Authentication Proxy service before continuing on to the side by side configuration steps.
If y'all practice non use the Proxy Manager to edit your configuration and so we recommend using WordPad or another text editor instead of Notepad when editing the config file on Windows.
Configure the Proxy for Your Primary Authenticator
In this step, you'll ready the Proxy'southward primary authenticator — the arrangement which volition validate users' existing passwords. Decide which type of primary hallmark you lot'll be using, and create either an Active Directory/LDAP [ad_client] client section, or a RADIUS [radius_client] department equally follows.
Active Directory
To use Active Directory/LDAP as your primary authenticator, add together an [ad_client] section to the top of your config file. Add together the following properties to the section:
host | The hostname or IP accost of your domain controller. |
service_account_username | The username of a domain business relationship that has permission to bind to your directory and perform searches. We recommend creating a service account that has read-but admission. |
service_account_password | The password corresponding to |
search_dn | The LDAP distinguished proper noun (DN) of an Active Directory container or organizational unit (OU) containing all of the users you wish to permit to log in. For example: |
host_2 | The hostname or IP accost of a secondary/fallback domain controller. You can add together additional domain controllers as |
security_group_dn | To further restrict admission, specify the LDAP distinguished proper name (DN) of a security grouping that contains the users who should be able to log in every bit straight group members. Nested groups are not supported. Users who are non straight members of the specified group will not laissez passer primary authentication. Example: Starting with Authentication Proxy v3.2.0, the |
username_attribute | LDAP attribute plant on a user entry which will contain the submitted username. In most Active Directory configurations, information technology should not be necessary to change this pick from the default value. OpenLDAP directories may utilise "uid" or another attribute for the username, which should exist specified with this pick. Default: "sAMAccountName" |
For case:
[ad_client] host=1.2.3.4 host_2=1.2.iii.v service_account_username=duoservice service_account_password=password1 search_dn=DC=example,DC=com security_group_dn=CN=DuoVPNUsers,OU=Groups,DC=instance,DC=com For avant-garde Agile Directory configuration, run into the full Hallmark Proxy documentation.
RADIUS
To use RADIUS as your master authenticator, add together a [radius_client] section to the height of your config file. So add the following properties to the section:
host | The IP accost of your RADIUS server. You can add together backup servers with |
secret | A secret to be shared between the Hallmark Proxy and your existing RADIUS server. If you're on Windows and would like to encrypt this secret, see Encrypting Passwords in the full Authentication Proxy documentation. |
port | The hallmark port on your RADIUS server. Utilise Default: |
pass_through_all | If this choice is set to Default: |
For example:
[radius_client] host=one.2.3.4 secret=radiusclientsecret In add-on, make sure that the RADIUS server is configured to accept authentication requests from the Hallmark Proxy.
For avant-garde RADIUS configuration, see the total Hallmark Proxy documentation.
Configure the Proxy for Your Citrix Gateway
Side by side, you demand to set up the Authentication Proxy to work with your Citrix Gateway or NetScaler. Create a [radius_server_iframe] department and add the properties listed below. If y'all've already fix upward the Duo Authentication Proxy for a different RADIUS iframe application, append a number to the section header to make it unique, like [radius_server_iframe2].
type | Either citrix_netscaler or citrix_netscaler_rfwebui:
Select the value that corresponds to your Gateway virtual server'south theme. If y'all customized theme, use the value that matches theme yous used for customization. | ||||||
api_host | Your API hostname (i.e. api-XXXXXXXX.duosecurity.com) | ||||||
ikey | Your Duo Citrix NetScaler integration key | ||||||
skey | Your Duo Citrix NetScaler clandestine key | ||||||
failmode | Either prophylactic or secure:
| ||||||
client | The mechanism that the Authentication Proxy should use to perform principal authentication. This should stand for with the "client" section you created earlier.
This parameter is optional if you only have i "client" section. If you have multiple, each "server" section should specify which "client" to use. | ||||||
radius_ip_1 | The management host IP address of your (kickoff) Citrix Gateway or NetScaler | ||||||
radius_secret_1 | A underground to be shared betwixt the proxy and your (outset) Citrix Gateway or NetScaler | ||||||
radius_ip_X | (Optional) IP addresses of additional Citrix Gateway or NetScaler management hosts (specified as radius_ip_2, radius_ip_3, etc.) | ||||||
radius_secret_X | (Optional) Secrets shared with additional Citrix Gateways or NetScalers (specified as radius_secret_2, radius_secret_3, etc.) | ||||||
port | Port on which to listen for incoming RADIUS Access Requests. If you have multiple RADIUS server sections yous should use a unique port for each one. Default: |
Configure the Proxy for Citrix Receiver or Workspace Client
Afterward that, you need to fix upwardly the Hallmark Proxy to piece of work with Citrix Receiver or Workspace client. Create a [radius_server_auto] section and add the properties listed below. If y'all've already prepare the Duo Authentication Proxy for a dissimilar RADIUS Automobile awarding, append a number to the section header to make it unique, like [radius_server_auto2].
api_host | Your API hostname (i.e. api-XXXXXXXX.duosecurity.com) | ||||||
ikey | Your Duo Citrix NetScaler integration key | ||||||
skey | Your Duo Citrix NetScaler secret key | ||||||
failmode | Either safe or secure:
| ||||||
client | The mechanism that the Authentication Proxy should use to perform primary authentication. This should correspond with the "client" department yous created earlier.
This parameter is optional if you lot only have one "customer" section. If you lot take multiple, each "server" department should specify which "customer" to use. | ||||||
radius_ip_1 | The management host IP address of your (get-go) Citrix Gateway or NetScaler | ||||||
radius_secret_1 | A surreptitious to exist shared between the proxy and your (first) Citrix Gateway or NetScaler | ||||||
radius_ip_X | (Optional) IP addresses of boosted Citrix Gateway or NetScaler management hosts (specified as radius_ip_2, radius_ip_3, etc.) | ||||||
radius_secret_X | (Optional) Secrets shared with boosted Citrix Gateway or NetScalers (specified as radius_secret_2, radius_secret_3, etc.) | ||||||
port | Port on which to listen for incoming RADIUS Access Requests. If y'all have multiple RADIUS server sections y'all should use a unique port for each one. Default: |
Note
The RADIUS port for the Citrix Receiver or Workspace client radius_server_auto section should not be the aforementioned RADIUS port used by the Gateway in the radius_server_iframe department of the authproxy.cfg file. For instance, if port 1812 is specified for radius_server_iframe, you might apply port 18120 for radius_server_auto.
A completed config file, using Active Directory as the principal authenticator, should look something similar:
[ad_client] host=ane.2.3.4 service_account_username=duoservice service_account_password=password1 search_dn=cn=Users,dc=case,dc=com [radius_server_iframe] type=citrix_netscaler ikey=DIXXXXXXXXXXXXXXXXXX skey=XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX api_host=api-XXXXXXXX.duosecurity.com failmode=safe client=ad_client radius_ip_1=5.6.7.viii radius_secret_1=thisisaradiussecret port=1812 [radius_server_auto] ikey=DIXXXXXXXXXXXXXXXXXX skey=XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX api_host=api-XXXXXXXX.duosecurity.com failmode=safe client=ad_client radius_ip_1=5.6.7.viii radius_secret_1=thisisaradiussecret port=18120 Brand sure to salve your configuration file when done.
Start the Proxy
- Windows
- Linux
If you lot installed the Duo Authentication Proxy Director utility (available with 5.6.0 and later), click the Start Service push button at the pinnacle of the Proxy Manager window to showtime the service.
To start the service from the command line, open an Administrator command prompt and run:
net get-go DuoAuthProxy Alternatively, open the Windows Services console (services.msc), locate "Duo Security Authentication Proxy Service" in the listing of services, and click the First Service button.
Authentication Proxy v5.1.0 and later includes the authproxyctl executable, which shows the connectivity tool output when starting the service. The installer adds the Hallmark Proxy C:\Program Files\Duo Security Hallmark Proxy\bin to your arrangement path automatically, so y'all should not need to specify the full path to authproxyctl to run it.
From an administrator control prompt run:
authproxyctl start If the service starts successfully, Hallmark Proxy service output is written to the authproxy.log file, which can exist found in the log subdirectory.
If you see an error proverb that the "service could not be started", open up the Application Event Viewer and look for an Error from the source "DuoAuthProxy". The traceback may include a "ConfigError" that can aid you find the source of the outcome.
End and restart the Authentication Proxy service by either clicking the Restart Service button in the Duo Hallmark Proxy Manager or the Windows Services console or issuing these commands from an Administrator control prompt:
net finish DuoAuthProxy & cyberspace start DuoAuthProxy To stop and restart the Authentication Proxy using authproxyctl, from an administrator command prompt run:
authproxyctl restart Open a root shell and run:
# /opt/duoauthproxy/bin/authproxyctl offset To ensure the proxy started successfully, run:
# /opt/duoauthproxy/bin/authproxyctl status Authentication Proxy service output is written to the authproxy.log file, which can exist found in the log subdirectory.
To stop and restart the Authentication Proxy, open up a root shell and run:
# /opt/duoauthproxy/bin/authproxyctl restart If you modify your authproxy.cfg configuration subsequently initial setup, y'all'll demand to stop and restart the Duo Hallmark Proxy service or process for your alter to have effect.
Configure Your Citrix Gateway
Before starting, check your Citrix Gateway web portal theme. The inline, browser-based Duo Prompt is compatible with the "Default" (aka "Caxton"), "Light-green Bubbles", "X1", and "RFWebUI" NetScaler themes (as well as custom themes based on ane of those built-in themes).
Learn more than about customizing the Citrix Gateway User Portal.
When creating your Citrix Gateway custom theme, use one of these built-in themes as the base for your customizations.
- Citrix Gateway 12.1 and xiii
- NetScaler 12
- NetScaler 10.five and 11
- Log in to the Citrix NetScaler authoritative interface.
- Navigate to NetScaler Gateway → Virtual Servers in the left panel of the administrative interface.
- Select your existing NetScaler Gateway Virtual Server, and then click Edit.
- On the "VPN Virtual Server" page, click the plus sign (+) next to Authentication to add together a new authentication policy.
-
On the "Choose Type" folio, select the RADIUS policy and Primary type from the drop-down menus and click Go along.
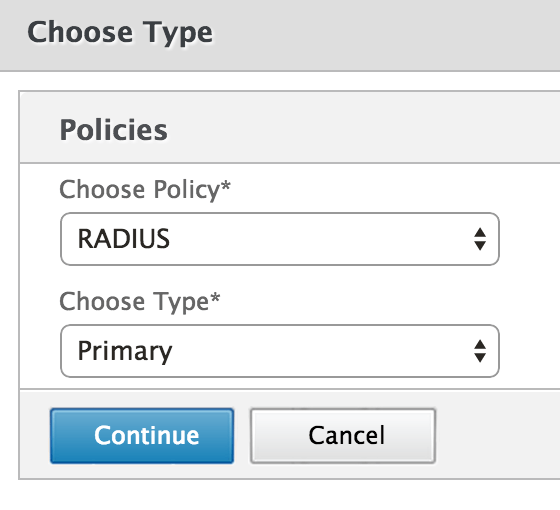
-
On the next "Choose Type" screen, click the plus sign (+) next to the "Policy Bounden" → "Select Policy" box.
-
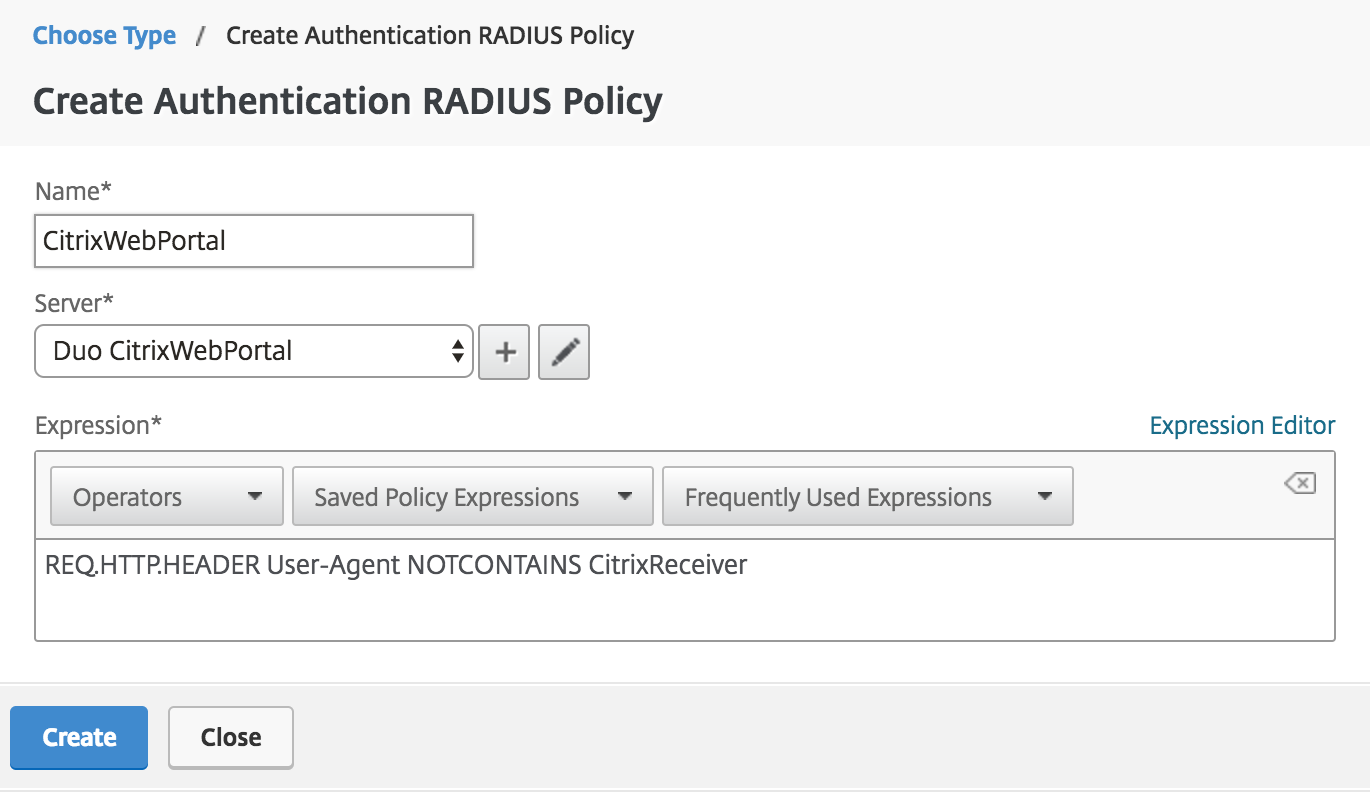
On the "Create Authentication RADIUS Policy" page, enter a proper noun for the policy (like CitrixWebPortal), and then click the plus sign (+) next to the "Server" box to create a new RADIUS server for Duo authentication for web browser clients.
-
On the "Create Hallmark RADIUS Server" folio, enter the information for your Duo Authentication Proxy server:
Name Duo CitrixWebPortal (or some descriptive proper name) Server Name or IP Address The hostname or IP address of your Duo Authentication Proxy server. Port The port configured for radius_server_iframe on the Duo Authentication Proxy (1812 in the example) Time-out (seconds) 60 Cloak-and-dagger Key The RADIUS cloak-and-dagger shared with your Duo Authentication Proxy Ostend Secret Cardinal The RADIUS hole-and-corner shared with your Duo Authentication Proxy 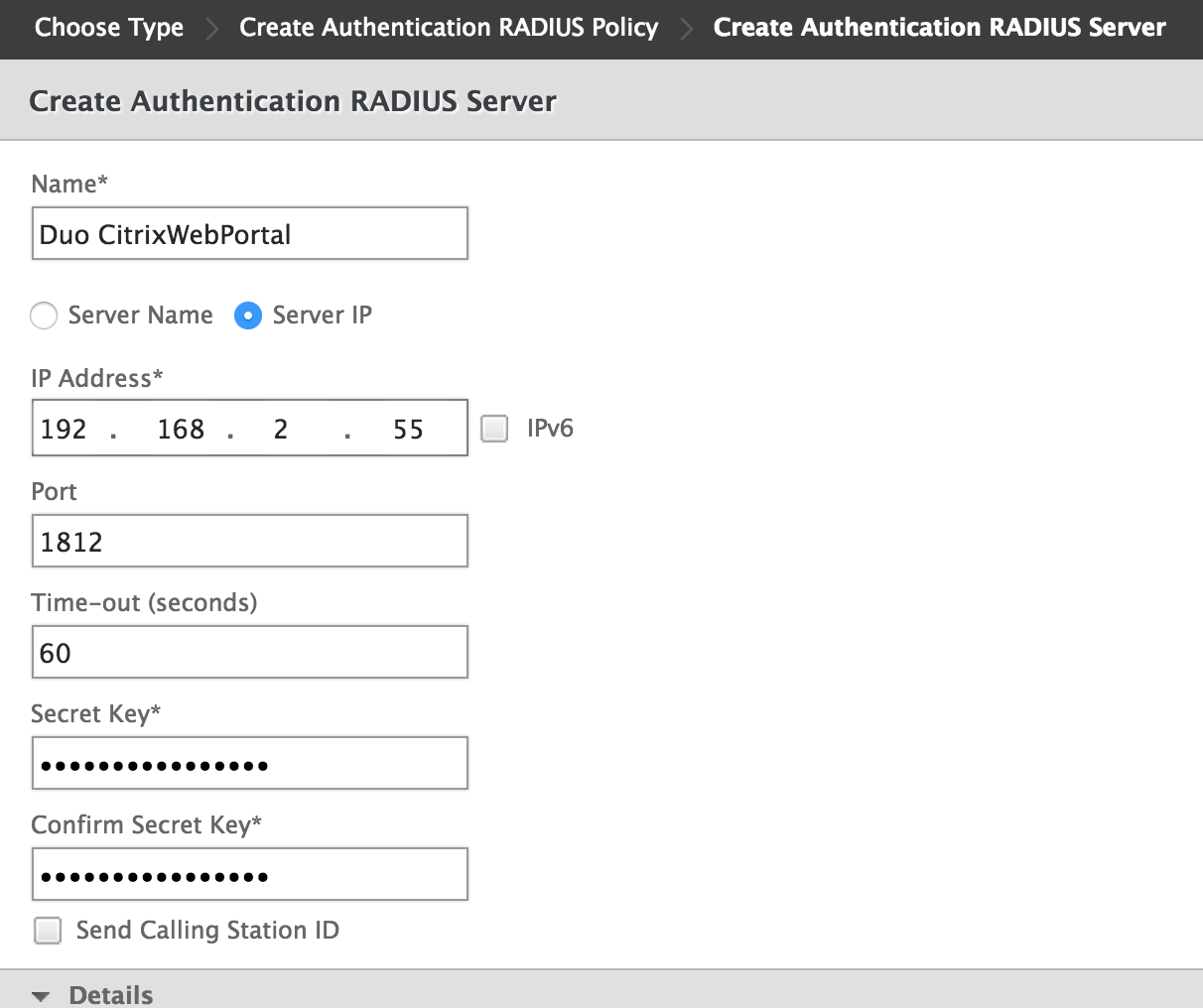
-
Click Create to add the Duo CitrixWebPortal RADIUS server and return to the "Create Authentication RADIUS Policy" page.
-
Click the Expression Editor link on the "Create Hallmark RADIUS Policy" page to add together an expression with the post-obit details:
Expression Type General Flow Type REQ Protocol HTTP Qualifier HEADER Operator NOTCONTAINS Value* CitrixReceiver Header Proper name* User-Agent 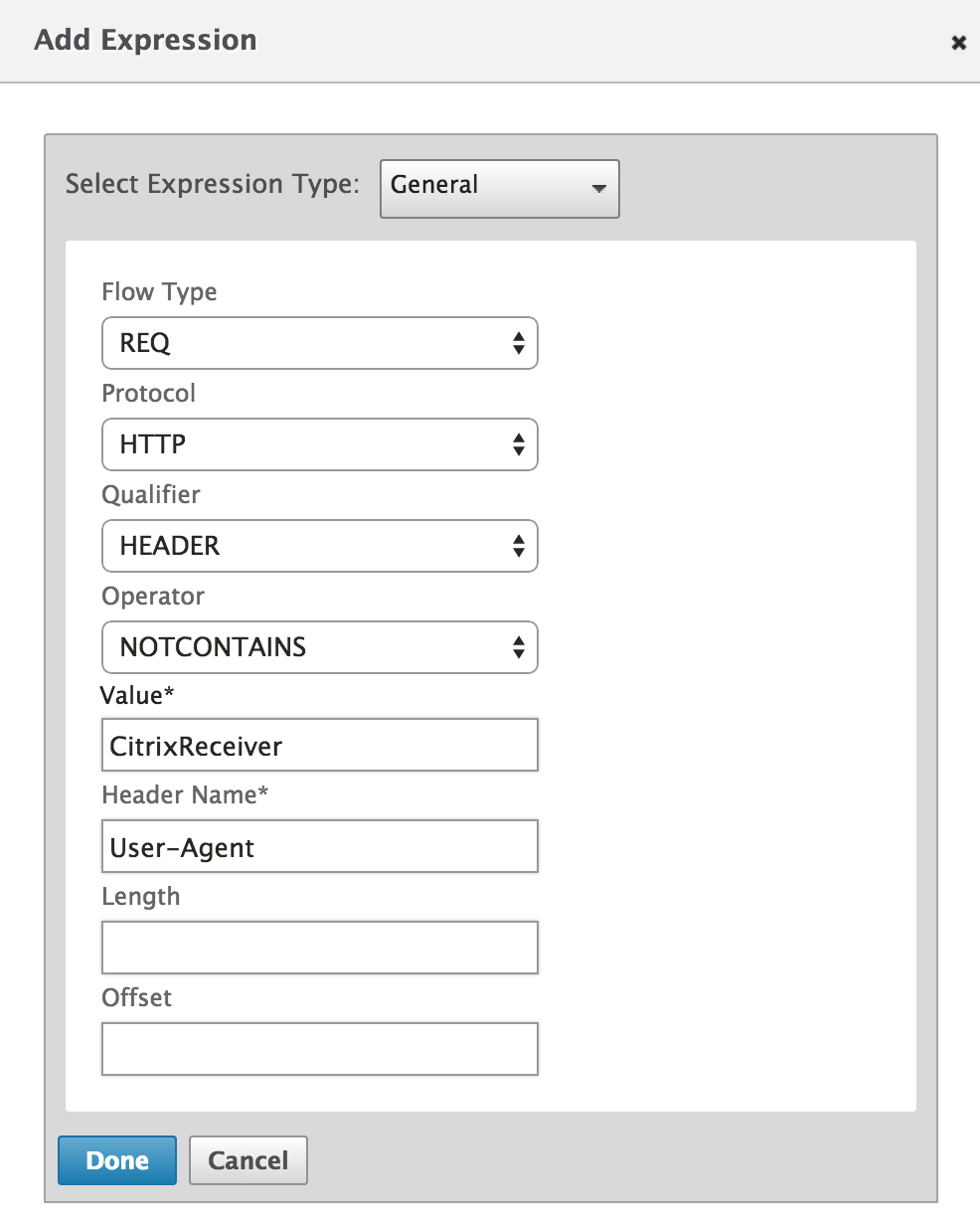
-
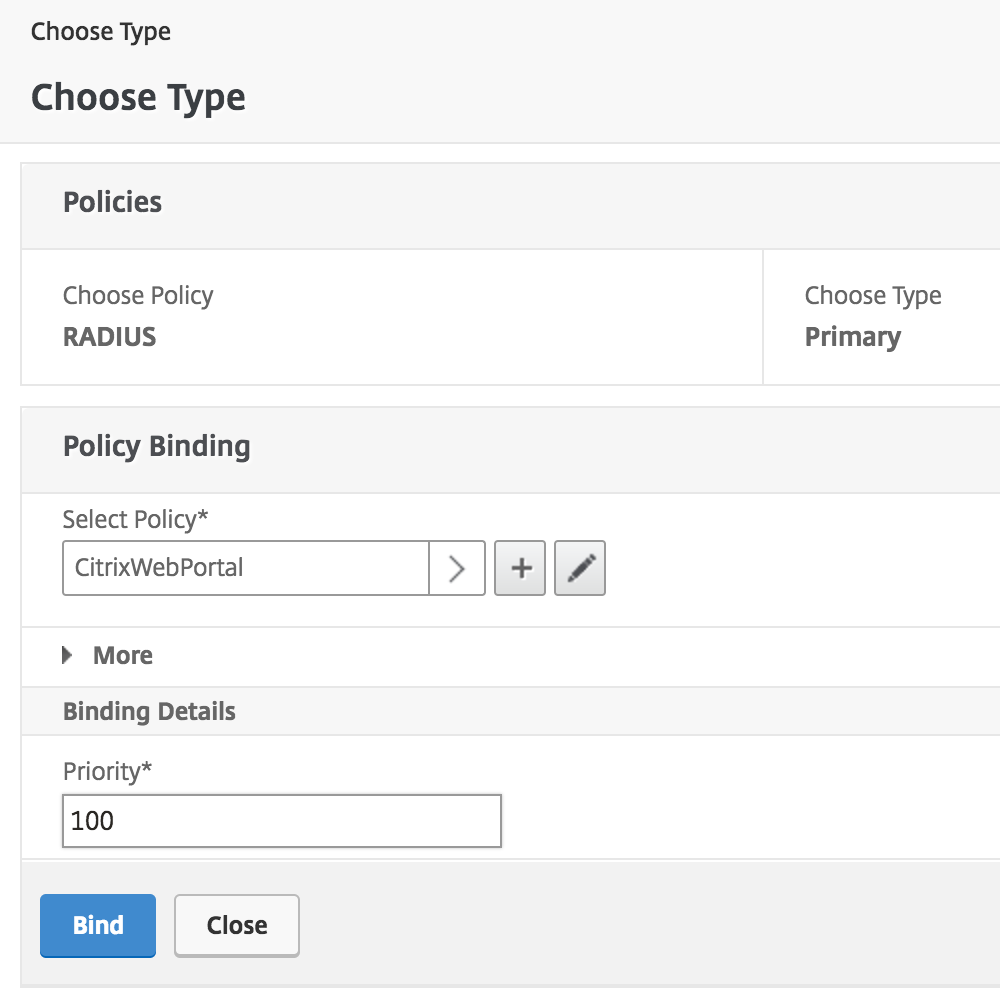
When the Server and Expression information is correct click Create to relieve the new CitrixWebPortal policy and return to the "Choose Type" page.
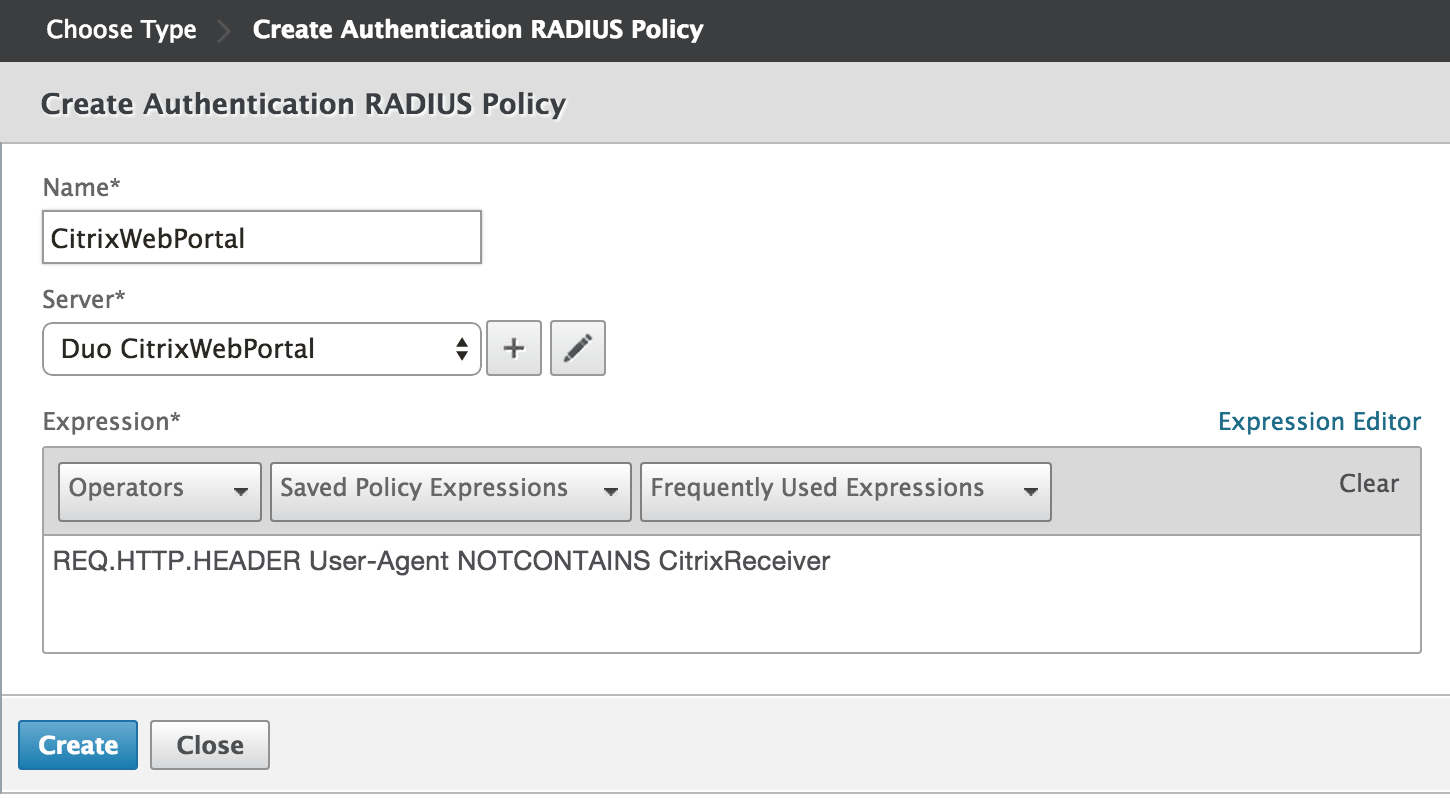
-
On the "Cull Type" folio, make sure the new RADIUS authentication policy you only created is selected. Set the Priority nether "Binding Details" to 100 and click Demark.
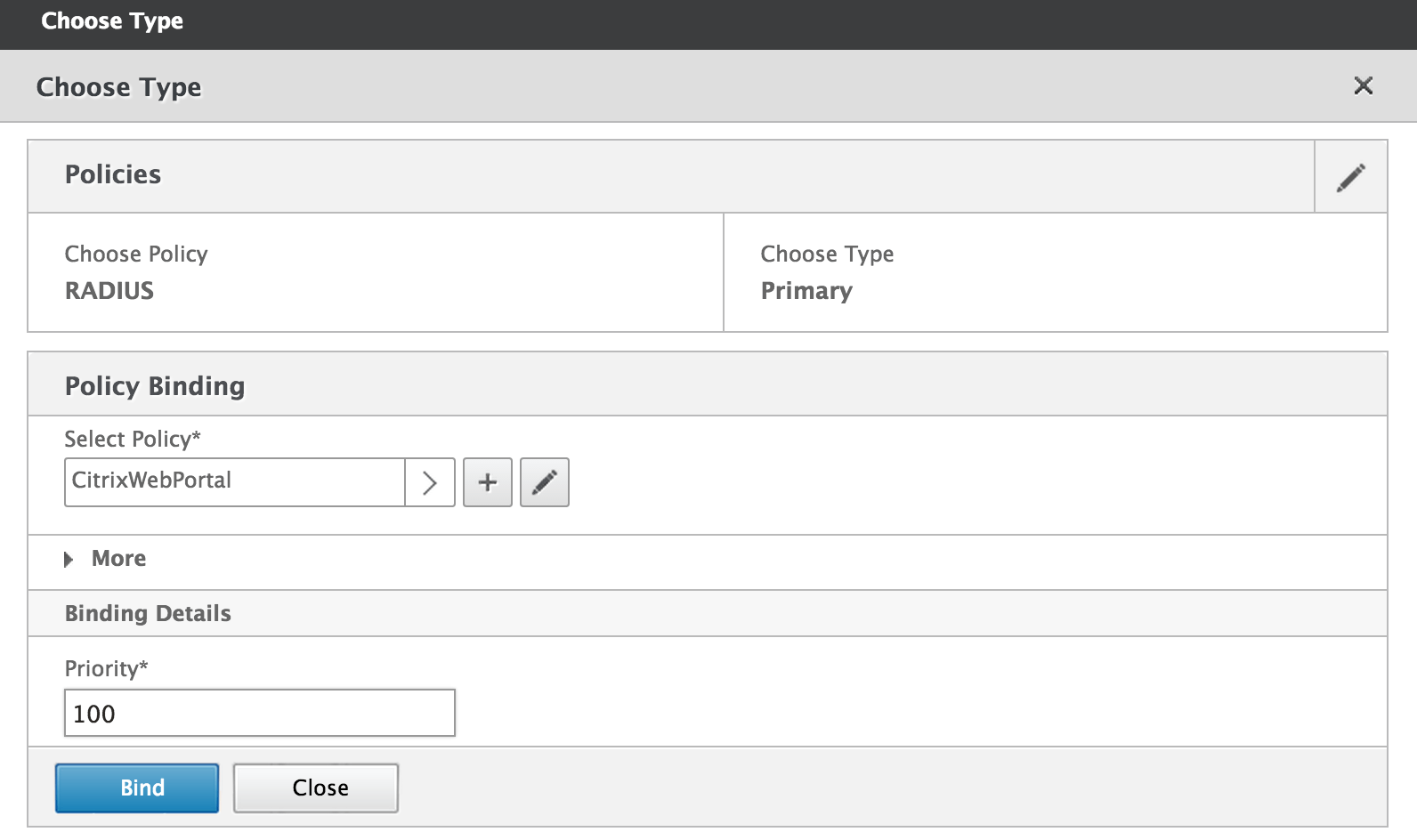
-
Binding the new hallmark policy returns you to the "VPN Virtual Server" page. Click the plus sign (+) next to Authentication over again to add a second new authentication policy.
-
On the "Choose Type" page, select the RADIUS policy and Primary type from the drop-down menus and click Continue.

-
On the adjacent "Choose Type" screen, click the Add Binding push.
-
Click the plus sign (+) next to the "Policy Binding" → "Select Policy" box.
-
On the "Create Authentication RADIUS Policy" page, enter a proper noun for the policy (like CitrixReceiver), and then click the plus sign (+) side by side to the "Server" box to create a new RADIUS server for Duo authentication for Citrix Receiver or Workspace clients.
-
On the "Create Authentication RADIUS Server" page, enter the information for your Duo Hallmark Proxy server:
Name Duo CitrixReceiver (or some descriptive name) Server Name or IP Accost The hostname or IP accost of your Duo Authentication Proxy server. Port The port configured for radius_server_auto on the Duo Authentication Proxy (18120 in the instance) Time-out (seconds) lx Hugger-mugger Key The RADIUS secret shared with your Duo Authentication Proxy Confirm Surreptitious Cardinal The RADIUS hush-hush shared with your Duo Authentication Proxy Send Calling Station ID Check this box in club to send the IP address of Citrix Receiver or Workspace clients to Duo 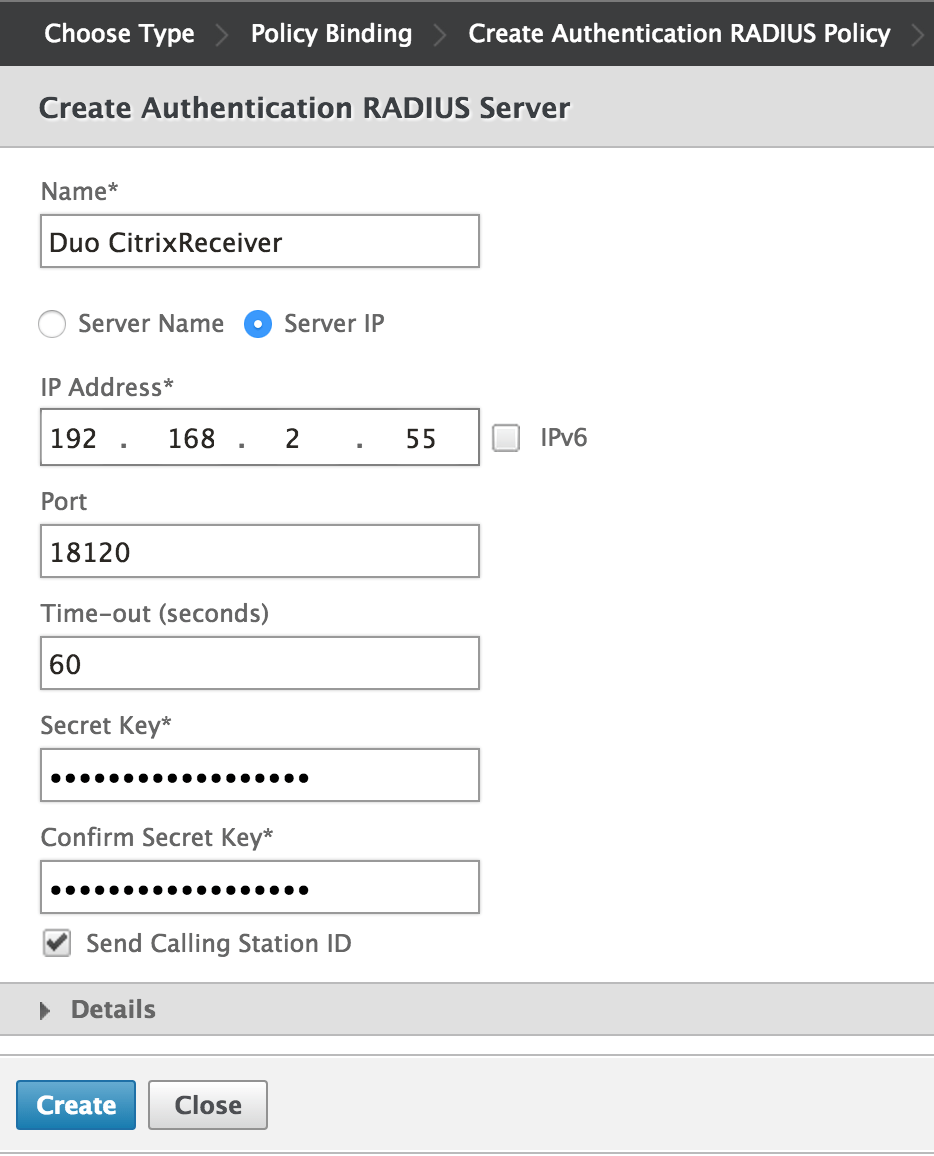
-
Click Create to add the Duo CitrixReceiver RADIUS server and return to the "Create Hallmark RADIUS Policy" page.
-
Click the Expression Editor link on the "Create Authentication RADIUS Policy" page to add an expression with the post-obit details:
Expression Type General Flow Blazon REQ Protocol HTTP Qualifier HEADER Operator CONTAINS Value* CitrixReceiver Header Name* User-Amanuensis 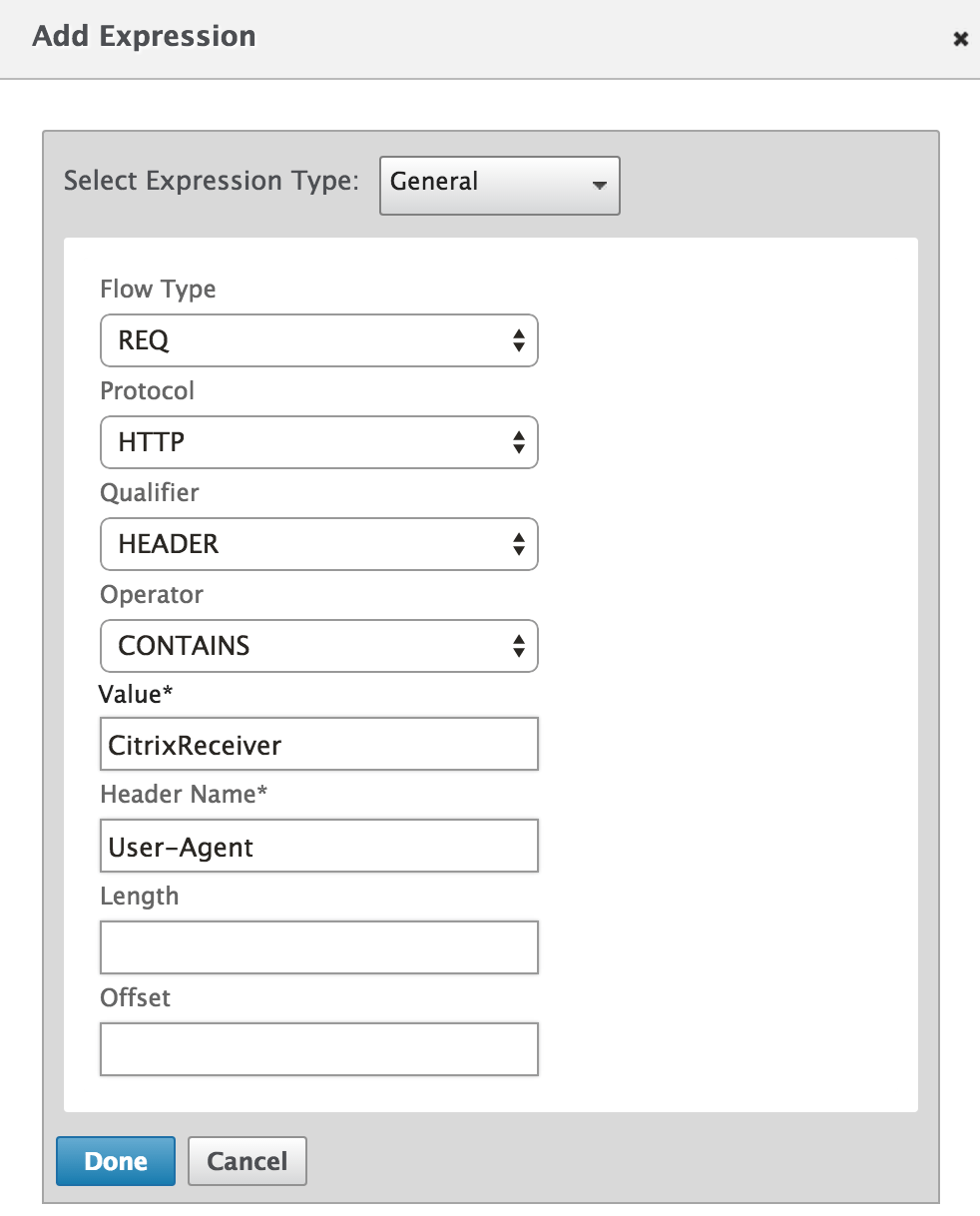
-
When the Server and Expression information is correct click Create to save the new CitrixReceiver policy and render to the "Choose Type" page.
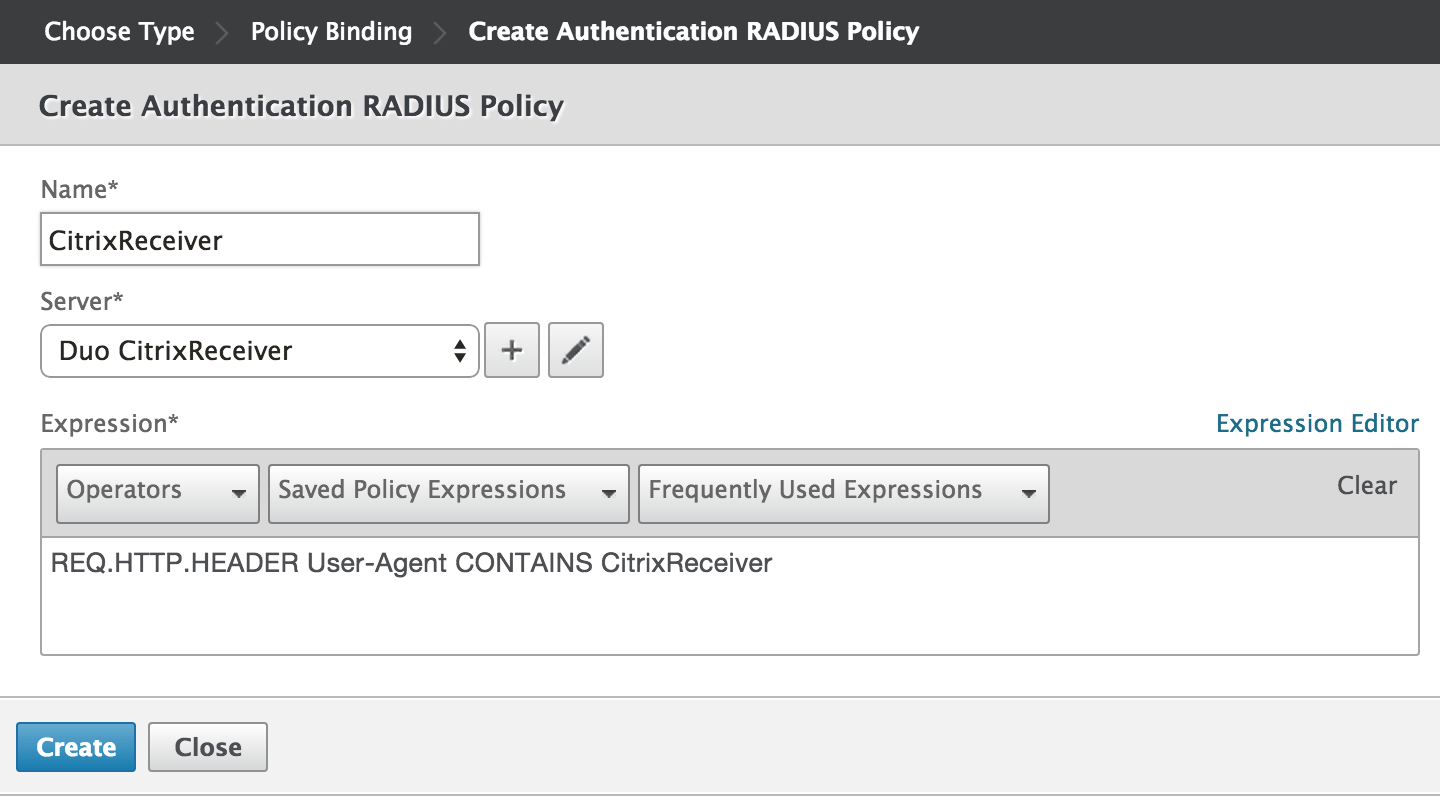
-
On the "Cull Blazon" page, make sure the new RADIUS authentication policy you just created is selected. Set the Priority under "Binding Details" to 110 and click Bind.
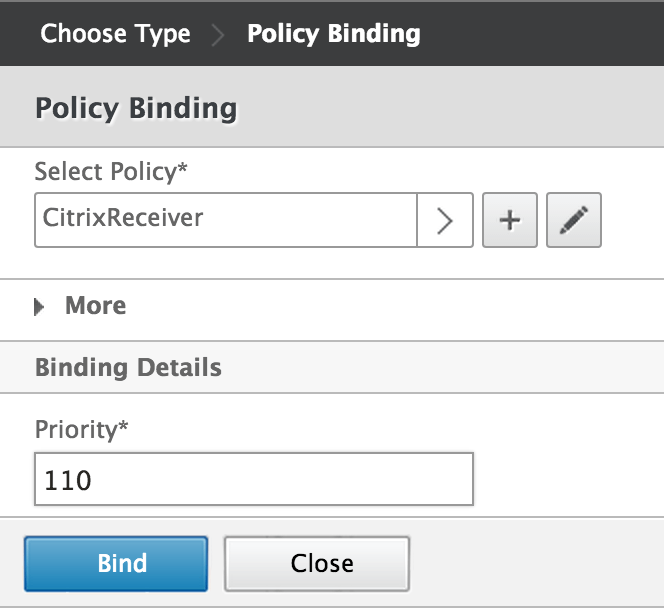
-
Verify that your new policies for Citrix Receiver or Workspace clients and browser clients are both listed and are bound in the correct guild. Click Close to save the new policy configuration.
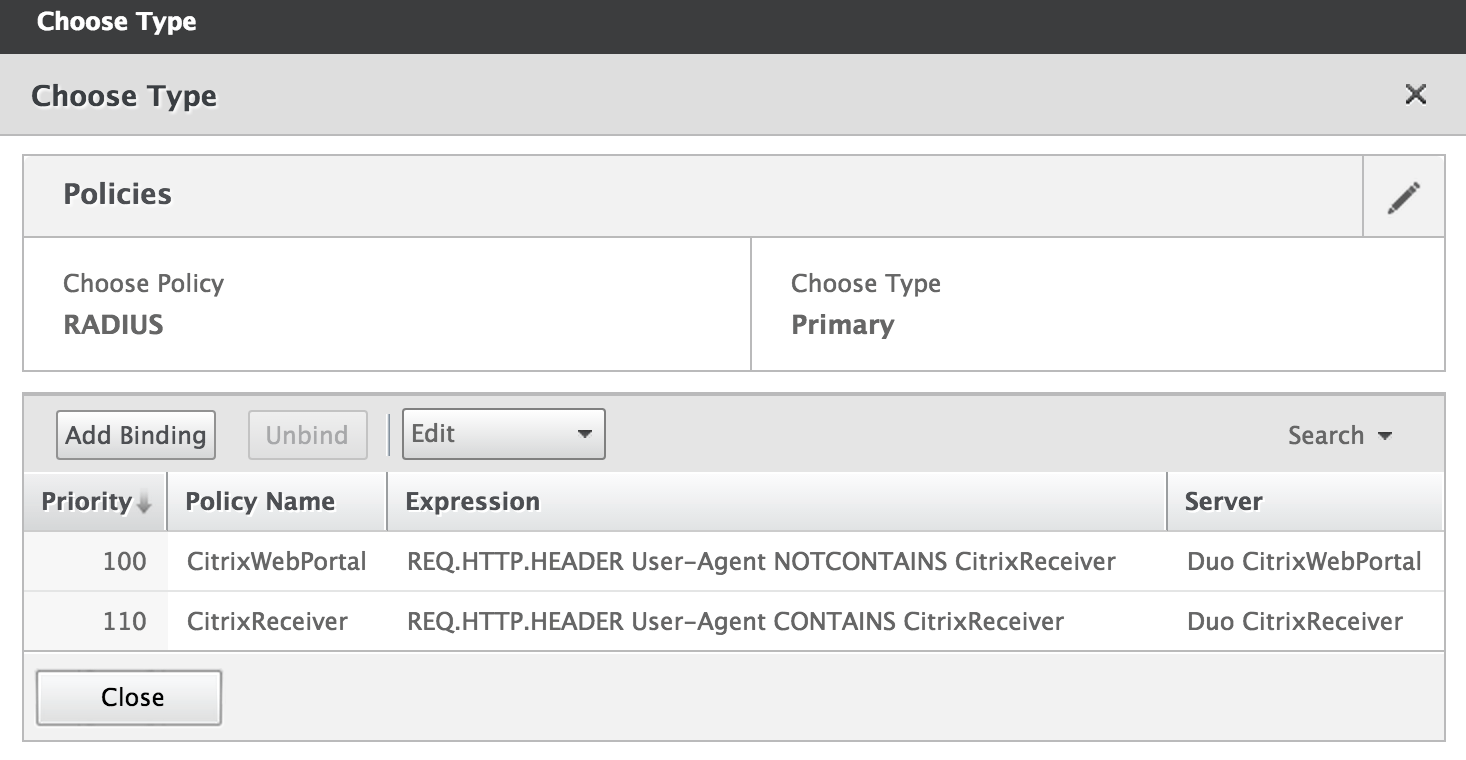
-
Verify that yous have ii RADIUS policies for Primary Authentication. Remove any other not-Duo primary hallmark policies (or increase the priority value then the NetScaler invokes Duo policies offset) and click Done.
-
Save all of the changes made to the running config.
- Log in to the Citrix NetScaler administrative interface.
- Navigate to NetScaler Gateway → Virtual Servers in the left panel of the administrative interface.
- Select your existing NetScaler Gateway Virtual Server, and and so click Edit.
- On the "VPN Virtual Server" page, click the plus sign (+) side by side to Basic Authentication to add a new hallmark policy.
-
On the "Cull Blazon" page, select the RADIUS policy and Chief blazon from the drop-downward menus and click Go on.
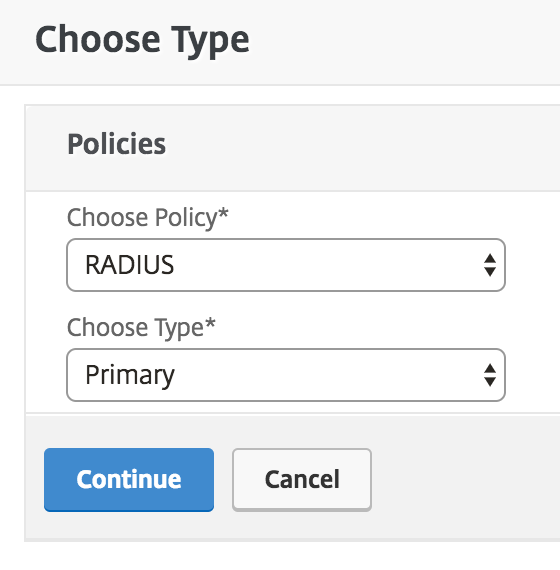
-
On the next "Choose Type" screen, click the plus sign (+) adjacent to the "Policy Bounden" → "Select Policy" box.
-
On the "Create Authentication RADIUS Policy" folio, enter a proper noun for the policy (like CitrixWebPortal), and so click the plus sign (+) side by side to the "Server" box to create a new RADIUS server for Duo authentication for web browser clients.
-
On the "Create Authentication RADIUS Server" page, enter the data for your Duo Hallmark Proxy server:
Name Duo CitrixWebPortal (or some descriptive proper name) Server Name or IP Address The hostname or IP address of your Duo Authentication Proxy server. Port The port configured for radius_server_iframe on the Duo Authentication Proxy (1812 in the case) Fourth dimension-out (seconds) 60 Secret Key The RADIUS hugger-mugger shared with your Duo Hallmark Proxy Confirm Secret Key The RADIUS secret shared with your Duo Authentication Proxy 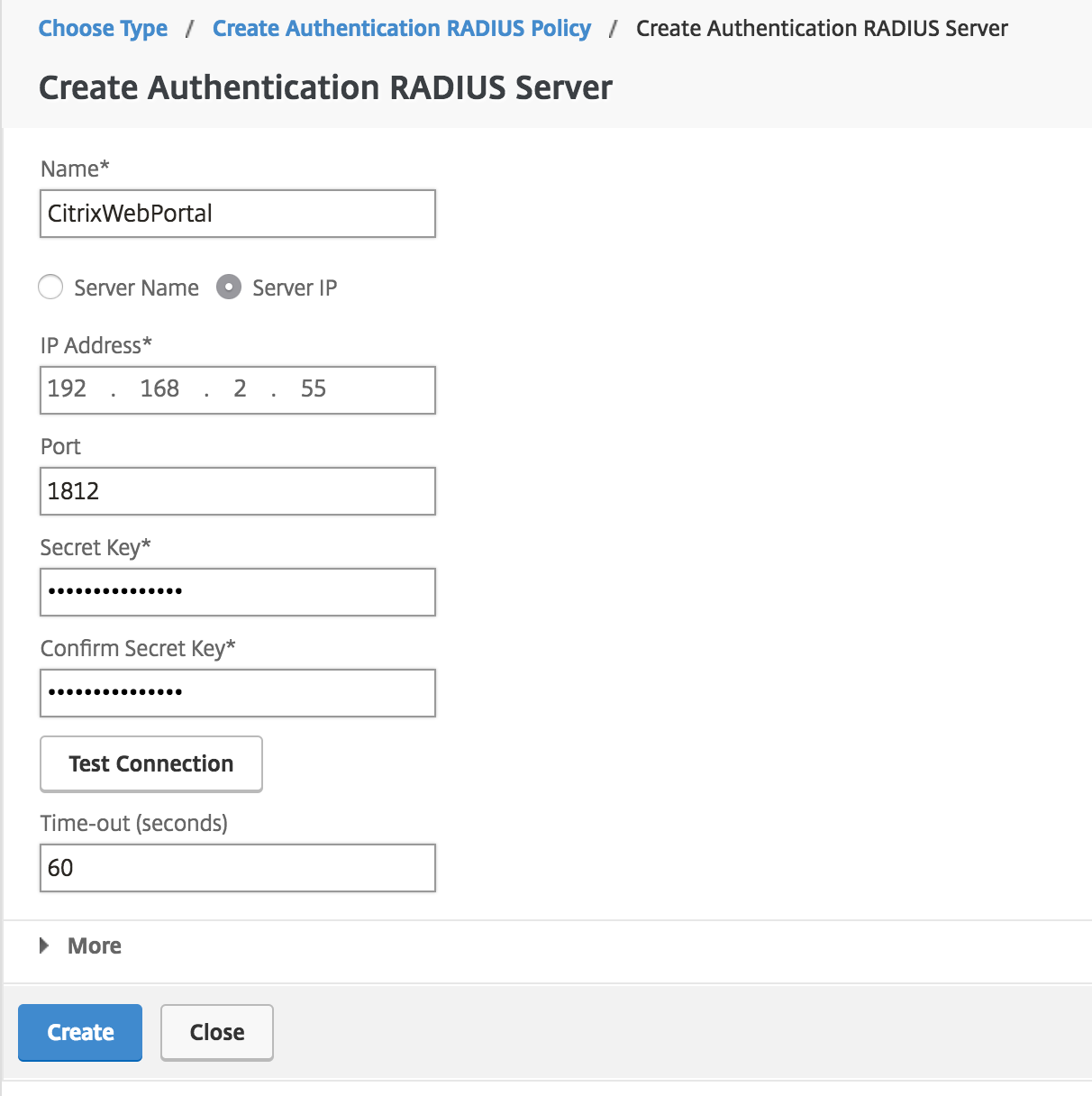
-
Click Create to add together the Duo CitrixWebPortal RADIUS server and return to the "Create Authentication RADIUS Policy" folio.
-
Click the Expression Editor link on the "Create Authentication RADIUS Policy" page to add an expression with the following details:
Expression Type General Flow Type REQ Protocol HTTP Qualifier HEADER Operator NOTCONTAINS Value* CitrixReceiver Header Proper noun* User-Agent 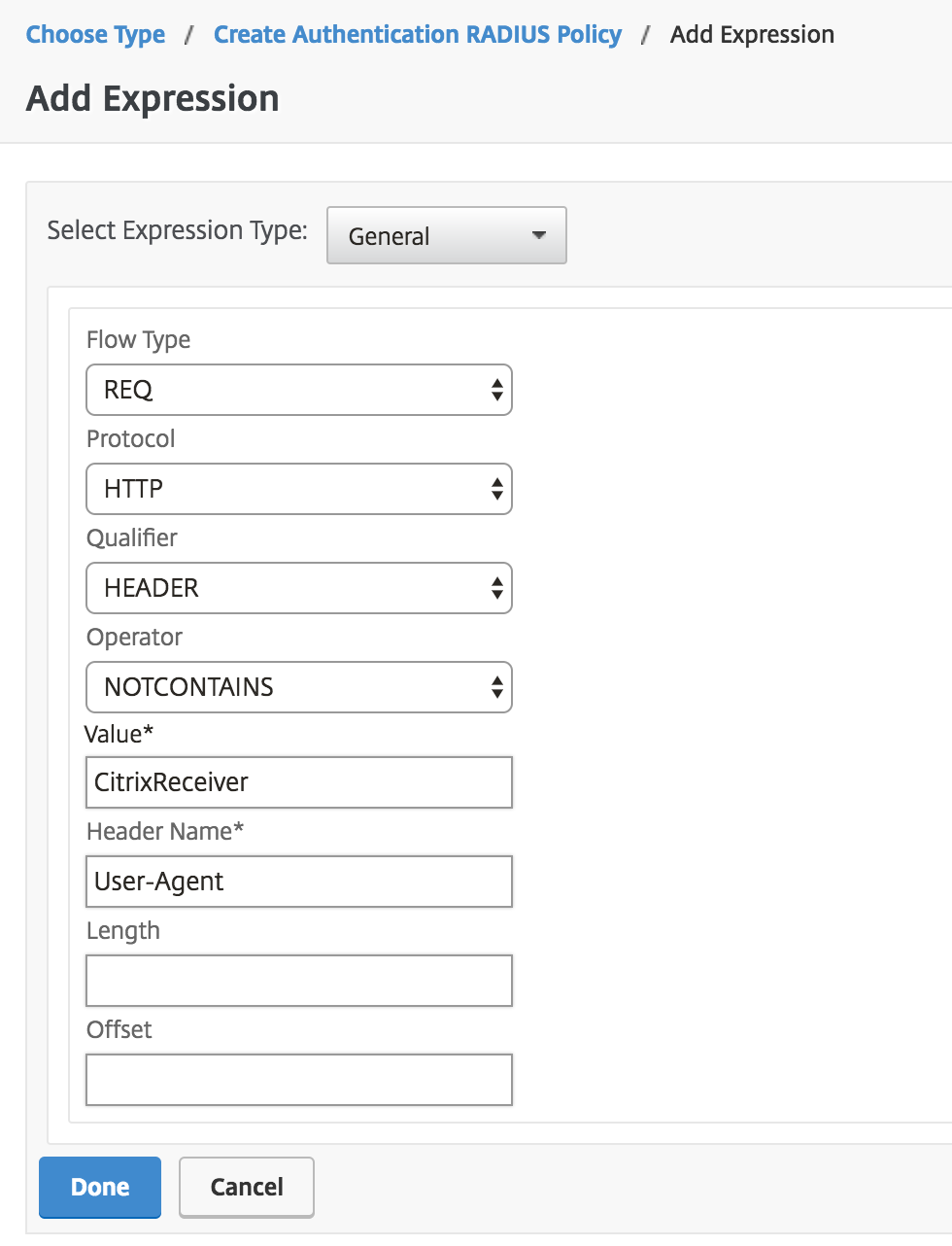
-
When the Server and Expression information is correct click Create to save the new CitrixWebPortal policy and return to the "Choose Blazon" folio.
-
On the "Choose Type" page, make sure the new RADIUS hallmark policy you just created is selected. Ready the Priority under "Binding Details" to 100 and click Bind.
-
Bounden the new authentication policy returns you lot to the "VPN Virtual Server" page. Click the plus sign (+) next to Authentication once more to add a 2d new authentication policy.
-
On the "Choose Type" folio, select the RADIUS policy and Principal type from the drop-downwards menus and click Proceed.

-
On the next "Cull Type" screen, click the Add Binding button.
-
Click the plus sign (+) adjacent to the "Policy Binding" → "Select Policy" box.
-
On the "Create Authentication RADIUS Policy" page, enter a name for the policy (like CitrixReceiver), and then click the plus sign (+) next to the "Server" box to create a new RADIUS server for Duo authentication for Citrix Receiver or Workspace clients.
-
On the "Create Authentication RADIUS Server" folio, enter the data for your Duo Hallmark Proxy server:
Proper noun CitrixReceiver (or some descriptive proper noun) Server Name or IP Address The hostname or IP address of your Duo Authentication Proxy server. Port The port configured for radius_server_auto on the Duo Hallmark Proxy (18120 in the example) Fourth dimension-out (seconds) 60 Hole-and-corner Cardinal The RADIUS secret shared with your Duo Authentication Proxy Ostend Secret Key The RADIUS surreptitious shared with your Duo Hallmark Proxy Send Calling Station ID Check this box in lodge to send the IP accost of Citrix Receiver or Workspace clients to Duo (click > More to expose this option) 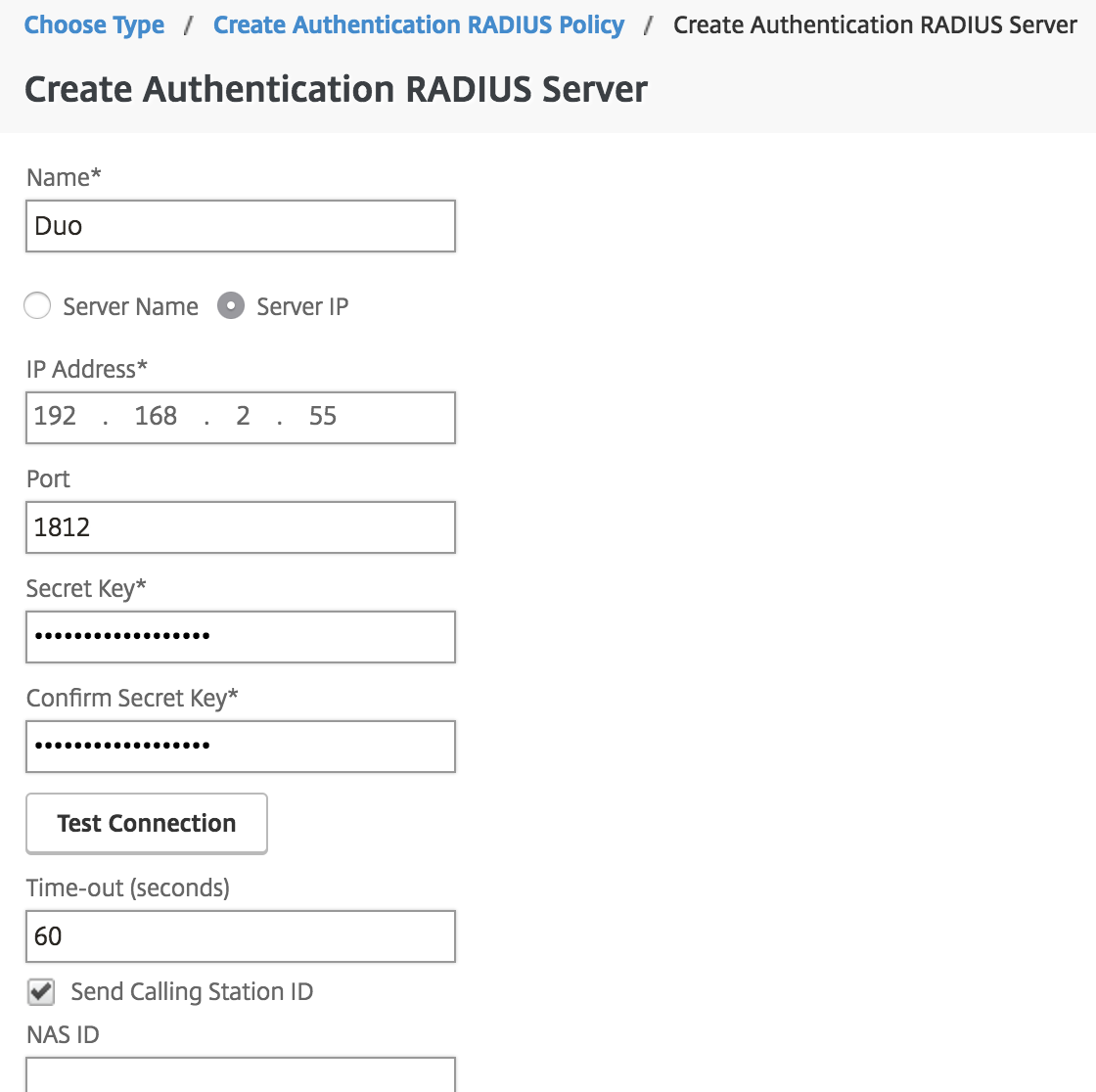
-
Click Create to add the CitrixReceiver RADIUS server and return to the "Create Authentication RADIUS Policy" page.
-
Click the Expression Editor link on the "Create Hallmark RADIUS Policy" page to add an expression with the following details:
Expression Type General Period Type REQ Protocol HTTP Qualifier HEADER Operator CONTAINS Value* CitrixReceiver Header Name* User-Agent 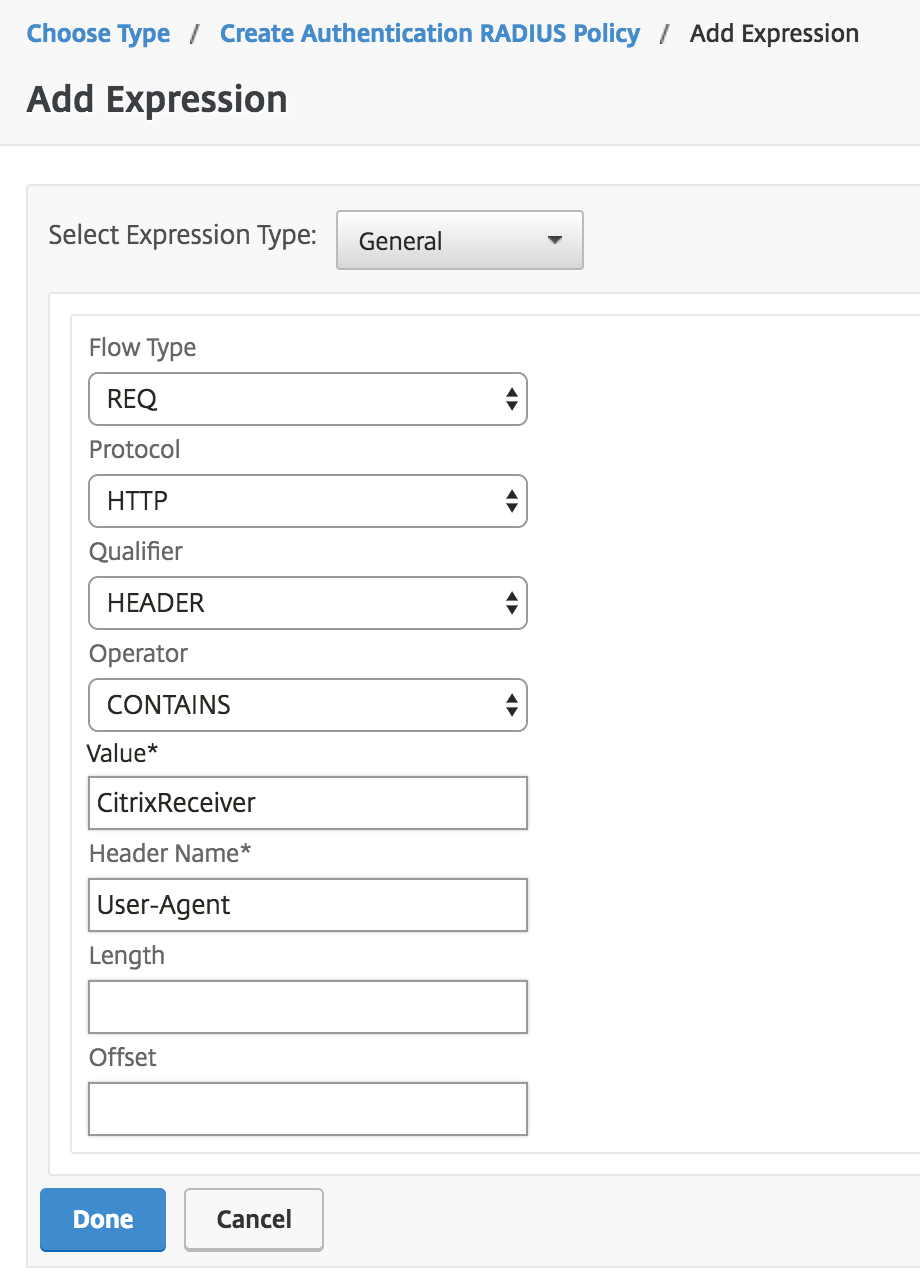
-
When the Server and Expression data is correct click Create to relieve the new CitrixReceiver policy and return to the "Choose Type" folio.
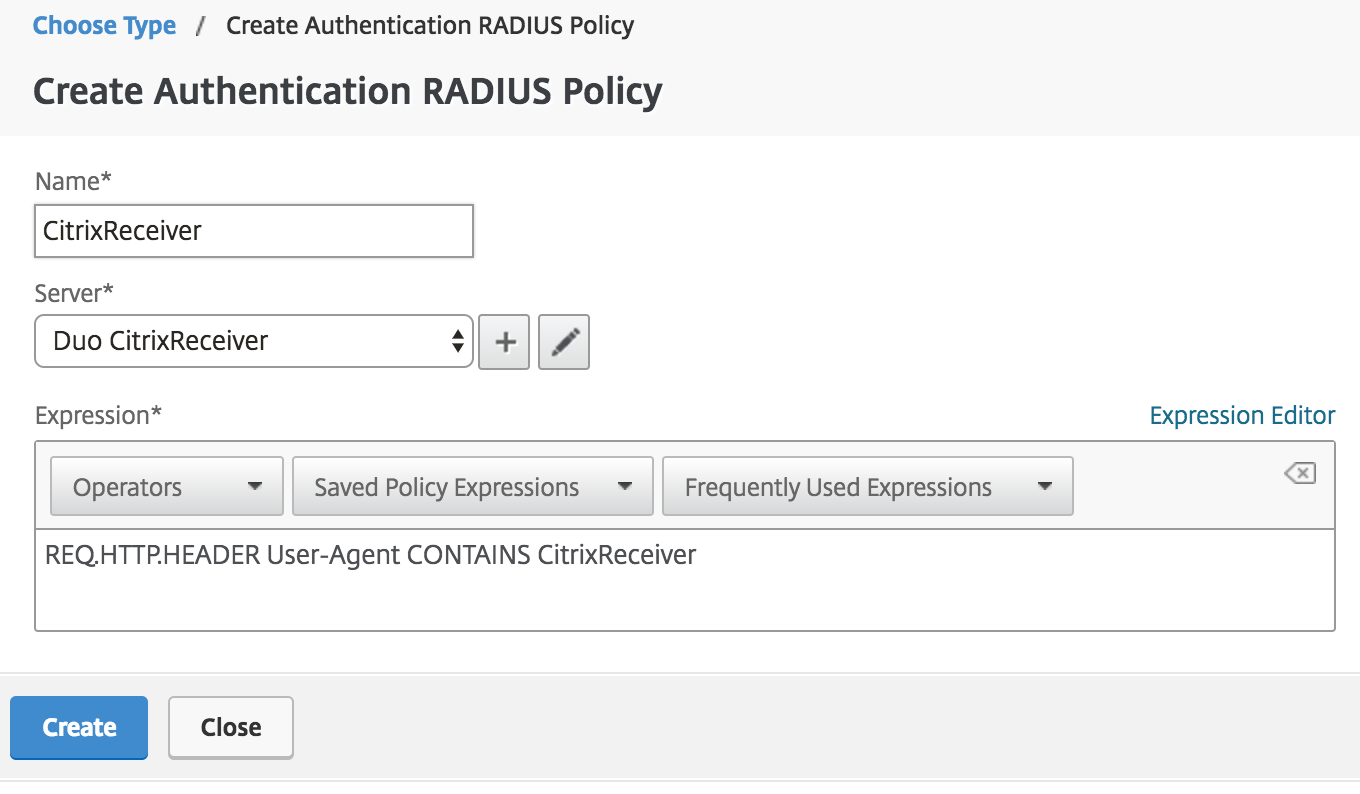
-
On the "Choose Type" page, make certain the new RADIUS hallmark policy you merely created is selected. Set up the Priority nether "Binding Details" to 110 and click Bind.
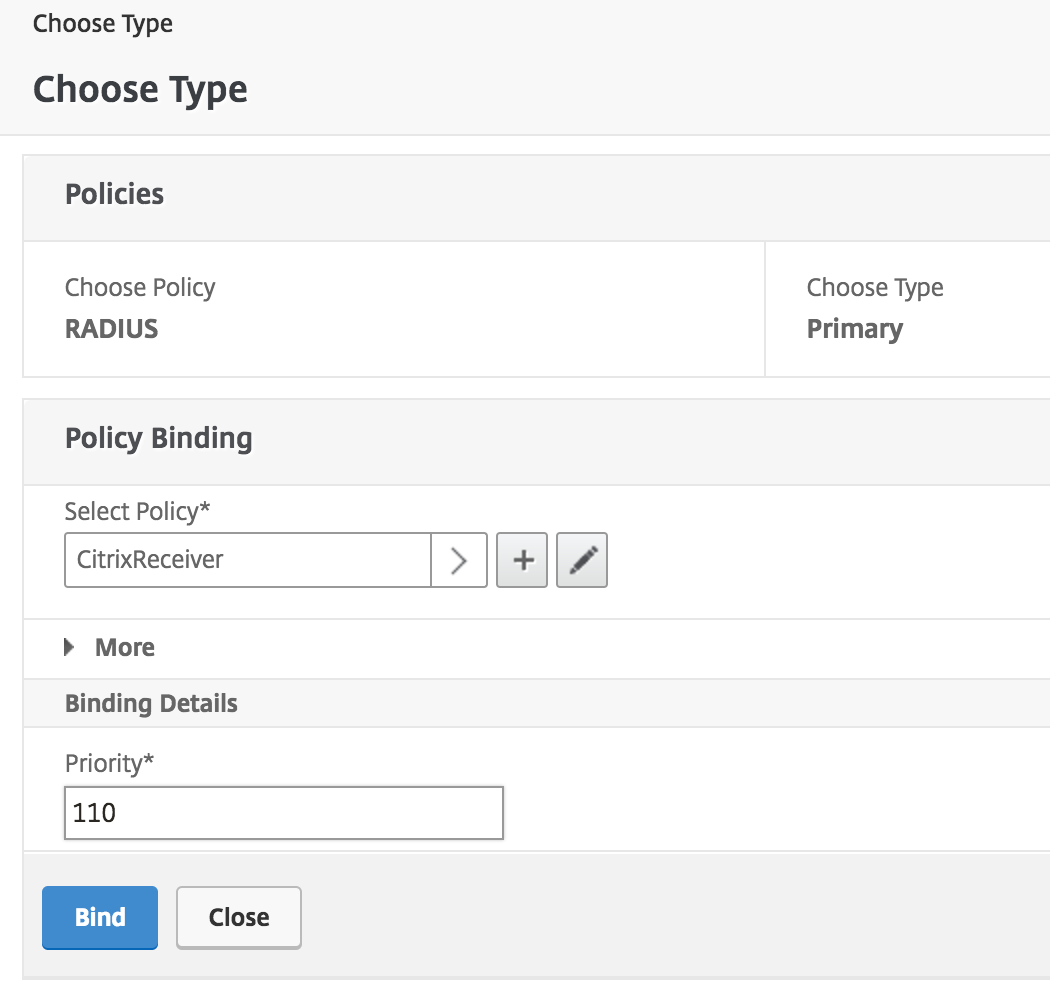
-
Verify that your new policies for Citrix Receiver or Workspace clients and browser clients are both listed and are spring in the right order. Click Close to save the new policy configuration.
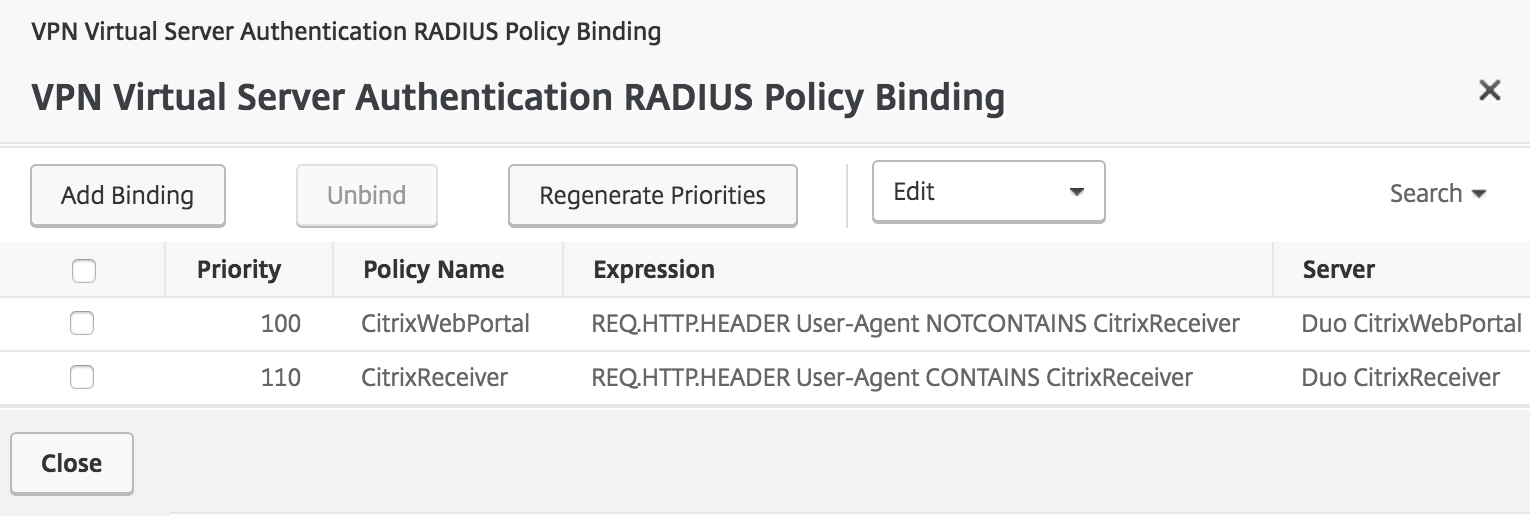
-
Verify that you have 2 RADIUS policies for Chief Authentication. Remove any other non-Duo primary authentication policies (or increase the priority value so the NetScaler invokes Duo policies first) and click Done.
-
Salvage all of the changes fabricated to the running config.
- Log in to the Citrix Gateway administrative interface.
- Navigate to Citrix Gateway → Virtual Servers in the left panel of the administrative interface.
- Select your existing Citrix Gateway Virtual Server, then click Edit.
- On the "VPN Virtual Server" page, click the plus sign (+) next to Basic Authentication to add a new hallmark policy.
-
On the "Choose Type" page, select the RADIUS policy and Main type from the drop-down menus and click Continue.

-
On the next "Choose Type" screen, click the plus sign (+) next to the "Policy Binding" → "Select Policy" box.
-
On the "Create Authentication RADIUS Policy" page, enter a proper name for the policy (like CitrixWebPortal), and then click the plus sign (+) adjacent to the "Server" box to create a new RADIUS server for Duo authentication for web browser clients.
-
On the "Create Authentication RADIUS Server" folio, enter the information for your Duo Authentication Proxy server:
Name Duo CitrixWebPortal (or some descriptive name) Server Proper name or IP Address The hostname or IP address of your Duo Hallmark Proxy server. Port The port configured for radius_server_iframe on the Duo Authentication Proxy (1812 in the case) Time-out (seconds) threescore Secret Key The RADIUS clandestine shared with your Duo Authentication Proxy Confirm Secret Key The RADIUS hush-hush shared with your Duo Authentication Proxy 
-
Click Create to add the Duo CitrixWebPortal RADIUS server and return to the "Create Hallmark RADIUS Policy" page.
-
Click the Expression Editor link on the "Create Hallmark RADIUS Policy" page to add together an expression with the following details:
Expression Type General Menstruation Type REQ Protocol HTTP Qualifier HEADER Operator NOTCONTAINS Value* CitrixReceiver Header Name* User-Amanuensis 
-
When the Server and Expression information is correct click Create to salvage the new CitrixWebPortal policy and return to the "Choose Blazon" page.

-
On the "Choose Blazon" page, make sure the new RADIUS authentication policy yous just created is selected. Set the Priority under "Binding Details" to 100 and click Bind.

-
Bounden the new authentication policy returns y'all to the "VPN Virtual Server" folio. Click the plus sign (+) adjacent to Authentication again to add together a 2d new authentication policy.
-
On the "Choose Type" page, select the RADIUS policy and Primary type from the drop-downwards menus and click Continue.

-
On the side by side "Cull Type" screen, click the Add Binding button.
-
Click the plus sign (+) next to the "Policy Binding" → "Select Policy" box.
-
On the "Create Authentication RADIUS Policy" folio, enter a name for the policy (similar CitrixReceiver), and and then click the plus sign (+) next to the "Server" box to create a new RADIUS server for Duo authentication for Citrix Receiver or Workspace clients.
-
On the "Create Authentication RADIUS Server" page, enter the information for your Duo Authentication Proxy server:
Name CitrixReceiver (or some descriptive name) Server Name or IP Accost The hostname or IP address of your Duo Authentication Proxy server. Port The port configured for radius_server_auto on the Duo Authentication Proxy (18120 in the example) Fourth dimension-out (seconds) 60 Secret Key The RADIUS secret shared with your Duo Hallmark Proxy Ostend Undercover Key The RADIUS clandestine shared with your Duo Hallmark Proxy Send Calling Station ID Check this box in order to send the IP accost of Citrix Receiver or Workspace clients to Duo (click > More to expose this choice) 
-
Click Create to add together the CitrixReceiver RADIUS server and return to the "Create Authentication RADIUS Policy" page.
-
Click the Expression Editor link on the "Create Authentication RADIUS Policy" page to add an expression with the following details:
Expression Type General Flow Type REQ Protocol HTTP Qualifier HEADER Operator CONTAINS Value* CitrixReceiver Header Name* User-Agent 
-
When the Server and Expression information is correct click Create to save the new CitrixReceiver policy and return to the "Cull Type" page.

-
On the "Choose Type" page, make sure the new RADIUS hallmark policy you just created is selected. Set the Priority under "Binding Details" to 110 and click Bind.

-
Verify that your new policies for Citrix Receiver or Workspace clients and browser clients are both listed and are bound in the right club. Click Close to save the new policy configuration.

-
Verify that you take two RADIUS policies for Main Authentication. Remove whatever other non-Duo principal authentication policies (or increase the priority value then the NetScaler invokes Duo policies offset) and click Done.
-
Save all of the changes made to the running config.
Test Your Setup
To test your setup, browse to the URL you normally use to log in to your Citrix Gateway. Later you complete primary authentication, the Duo enrollment/login prompt appears.
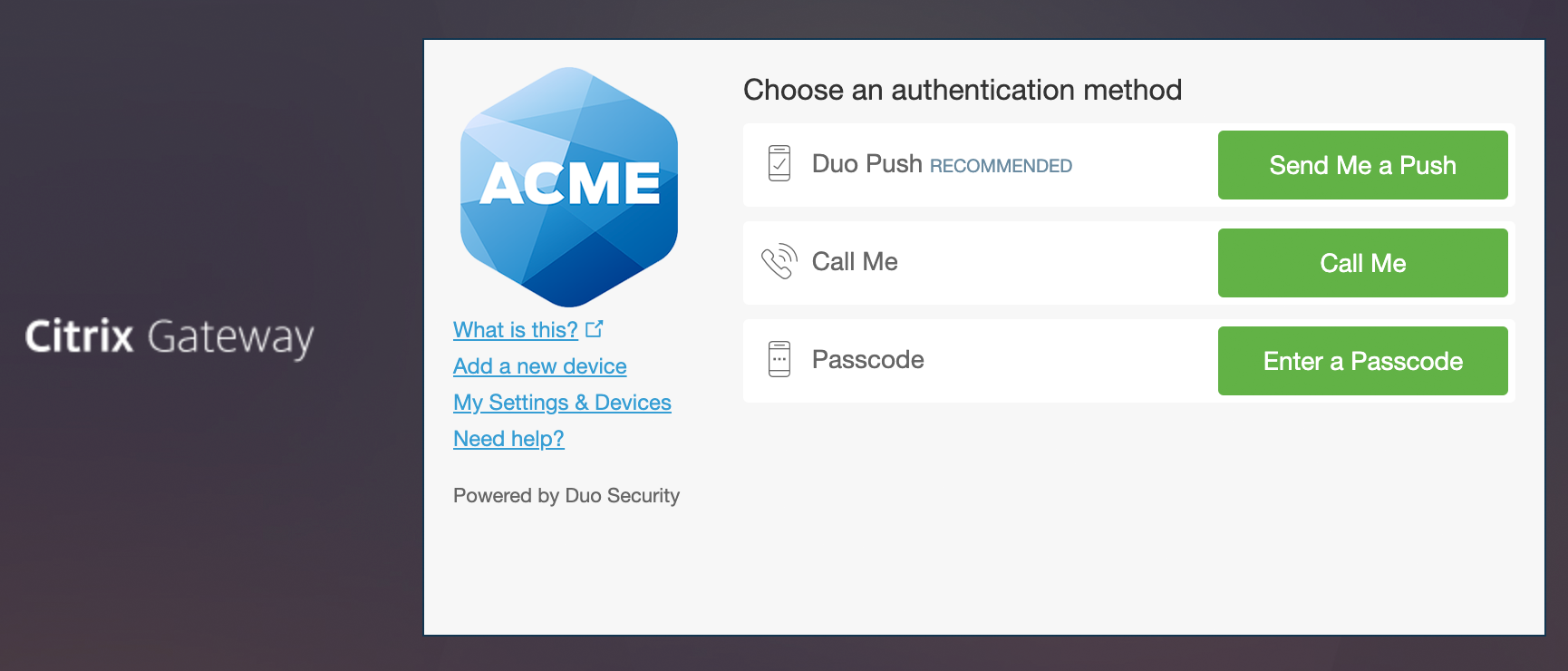
To test your setup with Citrix Receiver or Workspace client, attempt to log in to your newly-configured system. When you lot enter your username and countersign, yous will receive an automated push or telephone callback. Alternatively you can add a comma (",") to the end of your password, followed by a Duo passcode.
For example, given a username 'bob', with password 'password123' and a Duo passcode '123456', you would enter:
username: bob password: password123,123456 In addition, yous may besides enter the name of an out-of-band cistron in lieu of a passcode. Y'all may choose from the following factor names:
| push button | Perform Duo Push authentication You can use Duo Push if you've installed Duo Mobile and added your business relationship to it |
| phone | Perform phone callback authentication |
| sms | Ship a new batch of SMS passcodes Your authentication attempt will be denied. You tin then authenticate with one of the newly-delivered passcodes. |
Returning to the previous example, if yous wanted to use Duo Push button (rather than a passcode) to cosign, you would enter:
username: bob password: password123,push You can too specify a number subsequently the factor name if you lot have more than than one device enrolled. So you can enter phone2 or push2 if you accept two phones enrolled.
Troubleshooting
Need some help? Review troubleshooting tips for the Authentication Proxy and try the connectivity tool included with Duo Authentication Proxy 2.nine.0 and after to discover and troubleshoot general connectivity problems.
Also take a look at the Citrix Gateway or NetScaler Frequently Asked Questions (FAQ) page or endeavour searching our Citrix NetScaler Knowledge Base articles or Customs discussions. For further assist, contact Support.
Network Diagram
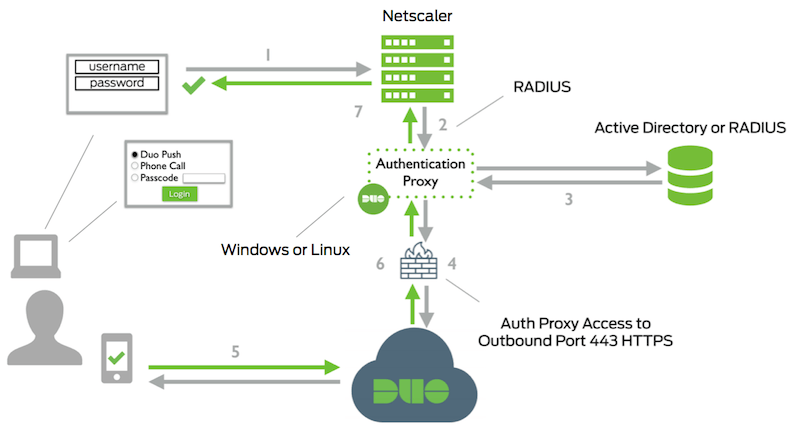
- Principal authentication initiated to Citrix Gateway
- Citrix Gateway send authentication request to Duo Security's hallmark proxy
- Primary hallmark using Active Directory or RADIUS
- Duo authentication proxy connection established to Duo Security over TCP port 443
- User completes Duo two-factor authentication via the interactive web prompt served from Duo'due south service or text input to the Citrix Gateway and their selected hallmark gene.
- Duo authentication proxy receives authentication response
- Citrix Gateway access granted
Source: https://duo.com/docs/citrix-netscaler
Posted by: frazierliblow.blogspot.com


0 Response to "How To Find Ip Address Of Citrix Server"
Post a Comment